WIN32 CONFICKER WORM REMOVAL TOOL FREE DOWNLOAD
But even those that are savvy computer uses and read the pop-up box carefully may still be mislead into thinking that they are opening a folder instead of actually running a file. Inherit from parent the permission entries that apply to child objects. Symantec Security Response encourages all users and administrators to adhere to the following basic security "best practices":. If device pairing must be used, ensure that all devices are set to "Unauthorized", requiring authorization for each connection request. These values are three numbers used respectively as multiplier M , divisor D , and additive A constant. Disable anonymous access to shared folders. These payload files are then saved in the registry and provided when other peers request them as well as allowing the payload files to be maintained when the compromised computer restarts. 
| Uploader: | Mezir |
| Date Added: | 16 June 2007 |
| File Size: | 34.92 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 56557 |
| Price: | Free* [*Free Regsitration Required] |
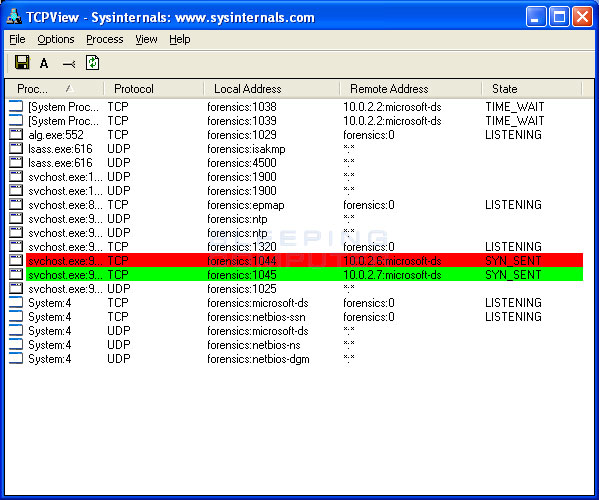
Tracking and finding Conficker infections Defending against the threat Conficker is now over 3 years old and is detected by all reputable antivirus software. Later variants of Conficker will create a named pipe at the following location: It also attempts to spread to network shares by brute-forcing commonly used network passwords and by copying itself to removable drives.
The functionality is 'awesome' and CCN X has matured nicely.
Once active the worm will attempt to determine the public IP address of the infected computer by visiting one or more of the following websites:. Note that your submission may not appear immediately on our site. Downadup, also known as Conficker by some news agencies and antivirus vendors, is an extremely interesting piece of malicious code and one of the most prolific worms in recent years. This site uses cookies to improve site functionality, for advertising purposes, and for website analytics.
confficker

Fortunately, most Windows XP and later systems will not provide this information by default and in those cases all of the user names on the local machine will be used instead. This threat is known to temoval spread by exploiting certain vulnerabilities.
CCN X for Mac - Free download and software reviews - CNET
This helps to prevent or limit damage when a computer is compromised. These include the following: Account lockout policies are being tripped.
Microsoft Security Bulletin MS confickker. While many of these modifications can be restored through various Windows components, it may be necessary to edit the registry.
How to remove Conficker Worm in 3 simple steps
The threat determines the version of Windows the remote host is running by fingerprinting the remote host by sending an SMB Session Setup Request. Sophos Anti-Virus detects and removes Conficker.
System Modifications The following side effects may be observed on computers compromised by members of this threat family. These payload files can then either cohficker saved to disk and executed or loaded directly to memory. Look at virtully any year.
Conficker Removal
Remoavl feature should be disabled so that removable devices do not execute when they are inserted into a computer. If that does not resolve the problem you can try one of the options available below.
What do you need to know about free software? Technical detail Cobficker is a worm for the Windows platform. This symptom was commonly reported in networks with computers infected by Downadup. If write access is not required, enable read-only mode if the option is available. Disable AutoPlay to prevent the automatic launching of executable files on network and removable drives, and disconnect the drives when not required.
The date timestamp is used re,oval an expiration date and if the file is past its expiration date, it is discarded. For further information on the terms used in this document, please refer to the Security Response glossary. Download now To prevent infection, Sophos recommends: B — that contained the missing GeoIP capability. Day Notes notes associated with a date just one click away with weekly, monthly and list views.
Crna Gora - Srpski. I like to keep track of special dates in the past and cconficker how long its been since the event took place - and this program lets me keep track very easily. Upon successful exploitation, the remote computer will then connect back to this URL and download the worm.
Indonesia Bahasa - Bahasa. CCN X is a comprehensive tool kit that brings together several essential features.

Comments
Post a Comment